Check Point Software Technologies Ltd. is an international provider of software and combined hardware and software products for IT security, including network security, endpoint security, data security and security management. HQ located in Tel Aviv, Israel, the company has development centers in Israel, California (ZoneAlarm), Sweden (Former Protect Data development centre), and Belarus. The company has main offices in the United States, in San Carlos, California, in Dallas, Texas, in Ottawa, Ontario, Canada, and Sydney Australia.
The company just recently disclosed details of a set of four vulnerabilities affecting Android smartphones and tablets that use Qualcomm® chipsets currently known as "QuadRooter".
It says that there are more than 900 million Android smartphones and tablets with Qualcomm chipsets. The flaw affects the top-end and most secure devices such as Samsung Galaxy S7 and BlackBerry DTEK50 as well. It can attack any smartphone with Android as OS and Qualcomm as a processor. So it is worth mentioning that QuadRooter flaw affects almost a billion Android-powered devices because if any one of the four vulnerabilities is exploited, an attacker can trigger privilege escalations for the purpose of gaining root access to a device, keylogging, GPS tracking, recording video and audio, unrestricted access to sensitive personal and enterprise data.
Qualcomm is the world’s leading designer of LTE chipsets with a 65% share of the LTE modem baseband market.
Security patches/updates by Qualcomm and Google
The security defect can provide intruders full control of affected
Android device. It can also provide access to personal and business
information. Hackers can take advantage of the flaw by tricking users
into downloading a malicious app. The installation of such app does not
even require special permissions, which makes hacker’s job easier. The
app grants hacker with a complete takeover of the device and lets them
fetch sensitive information. Without an advanced mobile threat detection and mitigation solution on
the Android device, there is little chance a user would suspect any
malicious behavior has taken place.
To clarify the issue, Qualcomm stated that it had fixed all the open-end vulnerabilities, and the security patches were handed over to the manufacturers. Google has included the fix for three vulnerabilities in the recent Android monthly security update. But one issue is still lingering, which will be cured in the September security update by Google. Also, as stated by Qualcomm, its clients already have the fixes, and they might roll it out soon.
To clarify the issue, Qualcomm stated that it had fixed all the open-end vulnerabilities, and the security patches were handed over to the manufacturers. Google has included the fix for three vulnerabilities in the recent Android monthly security update. But one issue is still lingering, which will be cured in the September security update by Google. Also, as stated by Qualcomm, its clients already have the fixes, and they might roll it out soon.
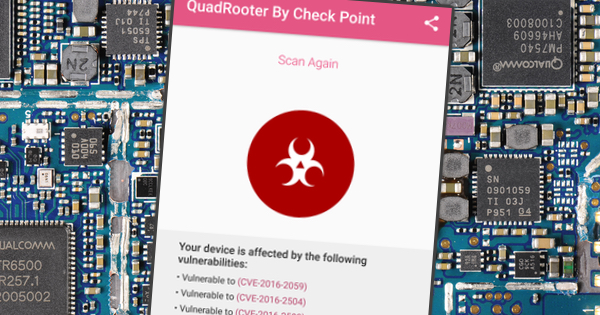
How to Scan for QuadRooter on your phone
Lucky you, before you get the Security update Check Point has launched a QuadRooter Scanner app on Google Play that would allow users to scan their device for vulnerabilities.
The app thoroughly examines the device and notifies the user whether
there are vulnerabilities or not.
In a blog post, Check Point wrote that smartphones such as Google’s Nexus 5X, Nexus 6, and Nexus 6P, HTC’s One M9 and HTC 10, and Samsung’s Galaxy S7 and S7 Edge are among many devices that are vulnerable to QuadRooter.
In a blog post, Check Point wrote that smartphones such as Google’s Nexus 5X, Nexus 6, and Nexus 6P, HTC’s One M9 and HTC 10, and Samsung’s Galaxy S7 and S7 Edge are among many devices that are vulnerable to QuadRooter.
To avoid QuadRooter, we recommend:
- Download and install the latest Android updates as soon as they become available. These include important security updates that help keep your device and data protected.
- Understand the risks of rooting your device – either intentionally or as a result of an attack.
- Examine carefully any app installation request before accepting it to make sure it’s legitimate.
- Avoid side-loading Android apps (.APK files) or downloading apps from third-party sources. Instead, practice good app hygiene by downloading apps only from Google Play.
- Read permission requests carefully when installing any apps. Be wary of apps that ask for permissions that seem unusual or unnecessary or that use large amounts of data or battery life.
- Use known, trusted Wi-Fi networks or while traveling use only those that you can verify are provided by a trustworthy source.
- End users and enterprises should consider using mobile security solutions designed to detect suspicious behavior on a device, including malware that could be obfuscated within installed apps.
- Lastly, download the QuadRooter Scanner app from Google Play and install it.




![List of Smartphones compatible with JTL Faiba4G and how to configure Faiba4G [Updated]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEikdB2PwQQQeIImGjcyfKZFQVNJIOZhEOx4Z3RpDpoFpFem4oAbU_SMTzRx_5U0F2i8aboMnNsIjmKQOTp39LM7lajjn3rsJ-7IvQRYbhEM5u2T9Y9zlrfHfvjbjQn4sPE96ZXK6w_KrgP_/s72-c/JTechpreneur_Smartphone+LTE+Compatible.png)


No comments:
Post a Comment